Question 1
Drag each item to its proper location
Place the BGP attributes in the correct order used for determining a route.
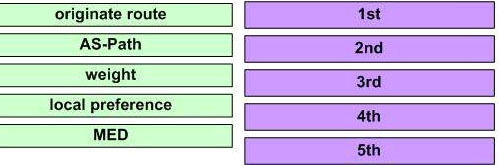
Answer:
Place the EIGRP commands to the proper locations
Answer:
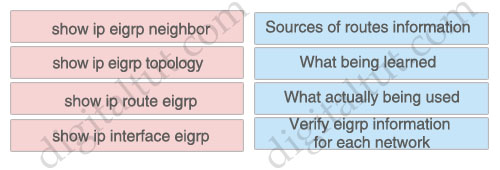
Sources of routes information: show ip eigrp neighbor
What being learned: show ip eigrp topology
What actually being used: show ip route eigrp
Verify eigrp information for each network: show ip interface eigrp
Question 4
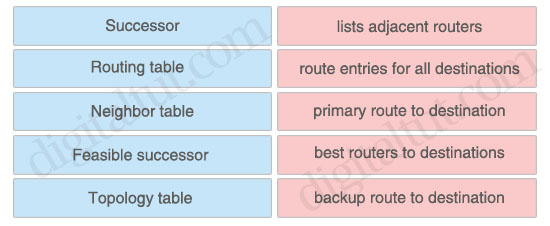
Place the EIGRP terms to the proper locations
Answer:
lists adjacent routers: Neighbor table
route entries for all destinations: Topology table
primary route to destination: Successor
best routers to destinations: Routing table
backup route to destination: Feasible successor
Question 5
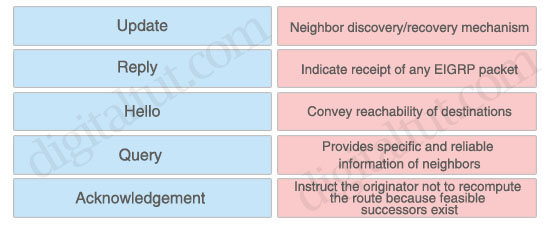
Place the EIGRP packets to the proper locations
 Answer:
Answer:
Neighbor discovery/recovery mechanism: Hello
Indicate receipt of any EIGRP packet: Acknowledgement
Convey reachability of destinations: Update
Provides specific and reliable information of neighbors: Query
Instruct the originator not to recompute the route because feasible successors exist: Reply
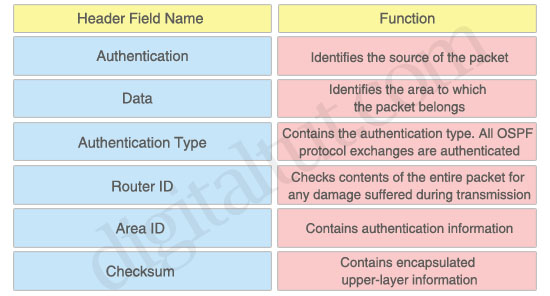
Question 6
Answer:
Identifies the source of the packet: Router ID
Identifies the area to which the packet belongs: Area ID
Contains the authentication type. All OSPF protocol exchanges are authenticated: Authentication Type
Checks contents of the entire packet for any damage suffered during transmission: Checksum
Contains authentication information: Authentication
Contains encapsulated upper-layer information: Data
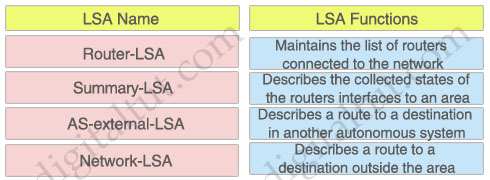
Question 7
 Answer:
Answer:
Maintains the list of routers connected to the network: Network-LSA
Describes the collected states of the routers interfaces to an area: Router-LSA
Describes a route to a destination in another autonomous system: AS-external-LSA
Describes a route to a destination outside the area: Summary-LSA
Question 8
A virtual private network (VPN) is a computer network that is layered on the top of an underlying computer network. VPNs are of different technologies, such as Trusted VPNs, Secure VPNs, and Hybrid VPNs, each having distinct requirements. Drag the various VPN names to their appropriate places.
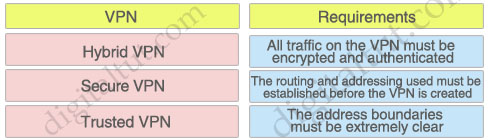 Answer:
Answer:
All traffic on the VPN must be encrypted and authenticated: Secure VPN
The routing and addressing used must be established before the VPN is created: Trusted VPN
The address boundaries must be extremely clear: Hybrid VPN
Question 9
IPv6 to IPv4 transition methods
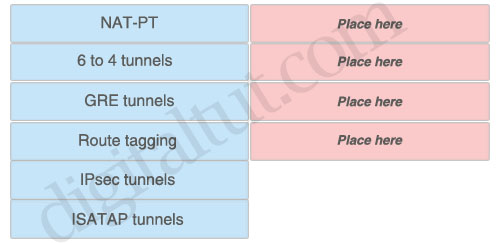 Answer:
Answer:
NAT-PT
6 to 4 tunnels
GRE tunnels
ISATAP tunnels
Question 10
IP tunneling is a method to encapsulate IP datagram within IP datagrams, which allows datagrams intended for one IP address to be wrapped and redirected to another IP address. IPv6 packets are encapsulated directly behind the IPv4 header. Drag the header fields to the appropriate places:
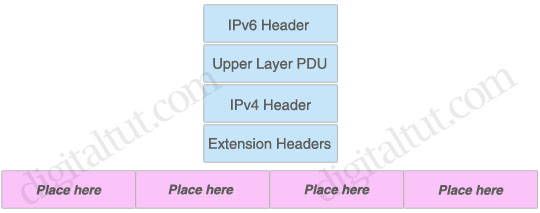
Answer:
The correct order is:
Explanation
The structure of a normal IPv6 packet is:
The IPv6 header is always present and is a fixed size of 40 bytes. Zero or more extension headers can be present and are of varying lengths. The upper layer protocol data unit (PDU) usually consists of an upper layer protocol header and its payload (for example, an ICMPv6 message, a UDP message, or a TCP segment).
Because “IPv6 packets are encapsulated directly behind the IPv4 header” so we can deduce an IPv4 Header must be placed before an IPv6 header.
Question 11
Drag each OSPF states into correct definition.
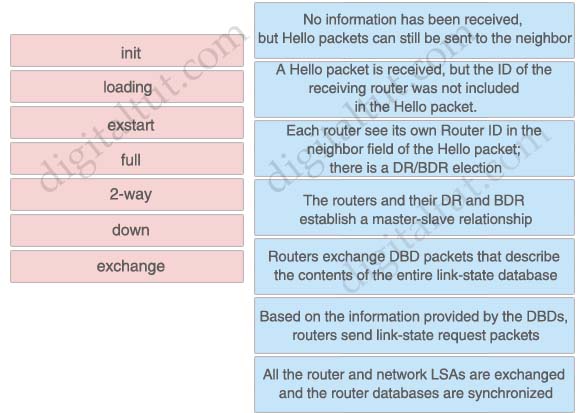
Answer and Explanation
The OSPF states below are described in the correct order when OSPF adjacency is formed:
Down: No information has been received, but Hello packets can still be sent to the neighbor
Init: A Hello packet is received, but the ID of the receiving router was not included in the Hello packet.
2-way: Each router see its own Router ID in the neighbor field of the Hello packet; there is a DR/BDR election.
Exstart: The routers and their DR and BDR establish a master-slave relationship.
Exchange: Routers exchange DBD packets that describe the contents of the entire link-state database.
Loading: Based on the information provided by the DBDs, routers send link-state request packets
Full: All the router and network LSAs are exchanged and the router databases are synchronized
A detailed explanation of OSPF states can be found here: http://www.cisco.com/c/en/us/support.../13685-13.html.
Question 12
Drag the “show” commands on the left to their proper locations on the right.
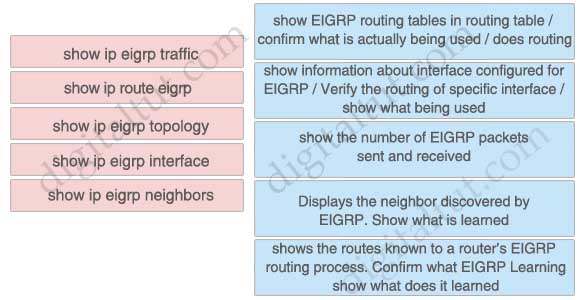
Answer:
+ show ip route eigrp: show EIGRP routing tables in routing table / confirm what is actually being used / does routing
+ show ip eigrp interface: show information about interface configured for EIGRP / Verify the routing of specific interface /
show what being used
+ show ip eigrp traffic: show the number of EIGRP packets sent and received
+ show ip eigrp neighbors: Displays the neighbor discovered by EIGRP. Show what is learned
+ show ip eigrp topology: shows the routes known to a router’s EIGRP routing process. Confirm what EIGRP Learning show what does it learned
Question 13
LSA corresponding area type.
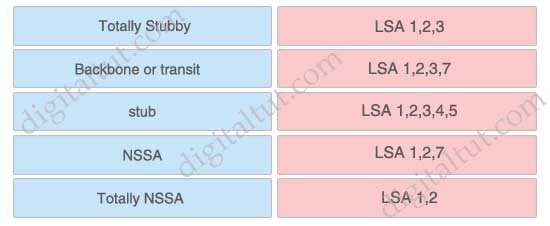
Answer:
+ stub: LSA 1,2,3
+ NSSA: LSA 1,2,3,7
+ Backbone or transit: LSA 1,2,3,4,5
+ Totally NSSA: LSA 1,2,7
+ Totally stubby: LSA 1,2
Question 14
Place the BGP attributes in the correct order used for determining a route.
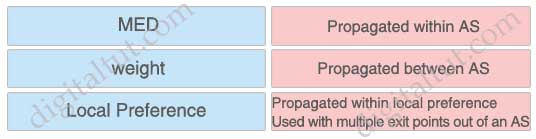
Answer:
+ MED: Propagated between AS
+ weight: Propagated within local preference / used with multiple exit points out of an AS
+ Local Preference: Propagated within AS
Question 15

Answer:
+ Bandwidth Management: low-speed WAN links
+ Authentication: WAN link to an external supplier
+ Redistribution: integrating two merging companies
+ Stubs: 256 kb/s CIR FR hub and spokes
Question 16
Click the resources on the left that you need to create an implementation plan for an OSPF project and drag them to the target zone on the right.
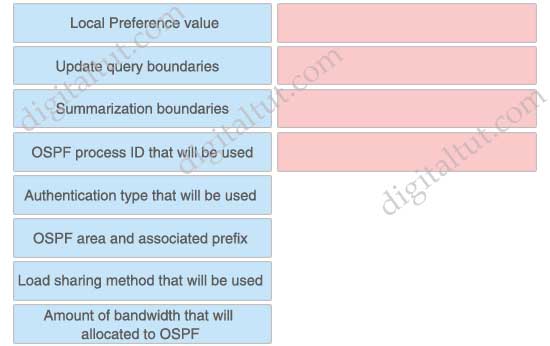
Answer:
+ Summarization boundaries
+ OSPF process ID that will be used
+ Authentication type that will be used
+ OSPF area and associated prefix
Question 17

Answer:
+ Which is used by router if route has more than one exit: weight
+ Which is not propagated in updates: weight
+ Which is spread through in the AS: local preference
+ Which goes to other AS: MED
Question 18
Click and drag the BGP attribute characterization on the left to the correct BGP attribute on the right.
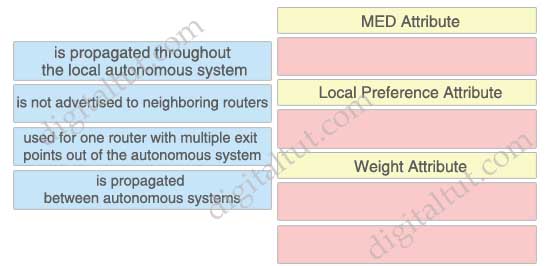
Answer:
Drag each item to its proper location
Place the BGP attributes in the correct order used for determining a route.

Answer:

Question 2
Place the BGP commands to the proper locations

Answer:
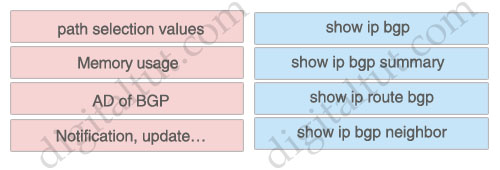
+ show ip bgp: path selection values
+ show ip bgp summary: Memory usage
+ show ip route bgp: AD of BGP
+ show ip bgp neighbor: Notification, update…
Question 3+ show ip bgp summary: Memory usage
+ show ip route bgp: AD of BGP
+ show ip bgp neighbor: Notification, update…
Place the EIGRP commands to the proper locations

Sources of routes information: show ip eigrp neighbor
What being learned: show ip eigrp topology
What actually being used: show ip route eigrp
Verify eigrp information for each network: show ip interface eigrp
Question 4
Place the EIGRP terms to the proper locations

Answer:
lists adjacent routers: Neighbor table
route entries for all destinations: Topology table
primary route to destination: Successor
best routers to destinations: Routing table
backup route to destination: Feasible successor
Question 5
Place the EIGRP packets to the proper locations

Neighbor discovery/recovery mechanism: Hello
Indicate receipt of any EIGRP packet: Acknowledgement
Convey reachability of destinations: Update
Provides specific and reliable information of neighbors: Query
Instruct the originator not to recompute the route because feasible successors exist: Reply
Question 6

Identifies the source of the packet: Router ID
Identifies the area to which the packet belongs: Area ID
Contains the authentication type. All OSPF protocol exchanges are authenticated: Authentication Type
Checks contents of the entire packet for any damage suffered during transmission: Checksum
Contains authentication information: Authentication
Contains encapsulated upper-layer information: Data
Question 7

Maintains the list of routers connected to the network: Network-LSA
Describes the collected states of the routers interfaces to an area: Router-LSA
Describes a route to a destination in another autonomous system: AS-external-LSA
Describes a route to a destination outside the area: Summary-LSA
Question 8
A virtual private network (VPN) is a computer network that is layered on the top of an underlying computer network. VPNs are of different technologies, such as Trusted VPNs, Secure VPNs, and Hybrid VPNs, each having distinct requirements. Drag the various VPN names to their appropriate places.

All traffic on the VPN must be encrypted and authenticated: Secure VPN
The routing and addressing used must be established before the VPN is created: Trusted VPN
The address boundaries must be extremely clear: Hybrid VPN
Question 9
IPv6 to IPv4 transition methods

NAT-PT
6 to 4 tunnels
GRE tunnels
ISATAP tunnels
Question 10
IP tunneling is a method to encapsulate IP datagram within IP datagrams, which allows datagrams intended for one IP address to be wrapped and redirected to another IP address. IPv6 packets are encapsulated directly behind the IPv4 header. Drag the header fields to the appropriate places:

Answer:
The correct order is:
| IPv4 Header | IPv6 Header | Extension Headers | Upper Layer PDU |
Explanation
The structure of a normal IPv6 packet is:
| IPv6 Header | Extension Headers | Upper Layer PDU |
Because “IPv6 packets are encapsulated directly behind the IPv4 header” so we can deduce an IPv4 Header must be placed before an IPv6 header.
Question 11
Drag each OSPF states into correct definition.

Answer and Explanation
The OSPF states below are described in the correct order when OSPF adjacency is formed:
Down: No information has been received, but Hello packets can still be sent to the neighbor
Init: A Hello packet is received, but the ID of the receiving router was not included in the Hello packet.
2-way: Each router see its own Router ID in the neighbor field of the Hello packet; there is a DR/BDR election.
Exstart: The routers and their DR and BDR establish a master-slave relationship.
Exchange: Routers exchange DBD packets that describe the contents of the entire link-state database.
Loading: Based on the information provided by the DBDs, routers send link-state request packets
Full: All the router and network LSAs are exchanged and the router databases are synchronized
A detailed explanation of OSPF states can be found here: http://www.cisco.com/c/en/us/support.../13685-13.html.
Question 12
Drag the “show” commands on the left to their proper locations on the right.

Answer:
+ show ip route eigrp: show EIGRP routing tables in routing table / confirm what is actually being used / does routing
+ show ip eigrp interface: show information about interface configured for EIGRP / Verify the routing of specific interface /
show what being used
+ show ip eigrp traffic: show the number of EIGRP packets sent and received
+ show ip eigrp neighbors: Displays the neighbor discovered by EIGRP. Show what is learned
+ show ip eigrp topology: shows the routes known to a router’s EIGRP routing process. Confirm what EIGRP Learning show what does it learned
Question 13
LSA corresponding area type.

Answer:
+ stub: LSA 1,2,3
+ NSSA: LSA 1,2,3,7
+ Backbone or transit: LSA 1,2,3,4,5
+ Totally NSSA: LSA 1,2,7
+ Totally stubby: LSA 1,2
Question 14
Place the BGP attributes in the correct order used for determining a route.

Answer:
+ MED: Propagated between AS
+ weight: Propagated within local preference / used with multiple exit points out of an AS
+ Local Preference: Propagated within AS
Question 15

Answer:
+ Bandwidth Management: low-speed WAN links
+ Authentication: WAN link to an external supplier
+ Redistribution: integrating two merging companies
+ Stubs: 256 kb/s CIR FR hub and spokes
Question 16
Click the resources on the left that you need to create an implementation plan for an OSPF project and drag them to the target zone on the right.

Answer:
+ Summarization boundaries
+ OSPF process ID that will be used
+ Authentication type that will be used
+ OSPF area and associated prefix
Question 17

Answer:
+ Which is used by router if route has more than one exit: weight
+ Which is not propagated in updates: weight
+ Which is spread through in the AS: local preference
+ Which goes to other AS: MED
Question 18
Click and drag the BGP attribute characterization on the left to the correct BGP attribute on the right.

Answer:
| MED Attribute | is propagated between autonomous systems |
| Local Preference Attribute | is propagated throughout the local autonomous system |
| Weight Attribute | + is not advertised to neighboring routers + used for one router with multiple exit points out of the autonomous system |