Question 1
Which item represents the standard IP ACL?
A. access-list 50 deny 192.168.1.1 0.0.0.255
B. access-list 110 permit ip any any
C. access-list 2500 deny tcp any host 192.168.1.1 eq 22
D. access-list 101 deny tcp any host 192.168.1.1
Answer: A
Explanation
The standard access lists are ranged from 1 to 99 and from 1300 to 1999 so only access list 50 is a standard access list.
Question 2
A network administrator is configuring ACLs on a Cisco router, to allow traffic from hosts on networks 192.168.146.0, 192.168.147.0, 192.168.148.0, and 192.168.149.0 only. Which two ACL statements, when combined, would you use to accomplish this task? (Choose two)
A. access-list 10 permit ip 192.168.146.0 0.0.1.255
B. access-list 10 permit ip 192.168.147.0 0.0.255.255
C. access-list 10 permit ip 192.168.148.0 0.0.1.255
D. access-list 10 permit ip 192.168.149.0 0.0.255.255
E. access-list 10 permit ip 192.168.146.0 0.0.0.255
F. access-list 10 permit ip 192.168.146.0 255.255.255.0
Answer: A C
Question 3
Refer to the exhibit.
An attempt to deny web access to a subnet blocks all traffic from the subnet. Which interface command immediately removes the effect of ACL 102?
A. no ip access-class 102 in
B. no ip access-class 102 out
C. no ip access-group 102 in
D. no ip access-group 102 out
E. no ip access-list 102 in
Answer: D
Question 4
On which options are standard access lists based?
A. destination address and wildcard mask
B. destination address and subnet mask
C. source address and subnet mask
D. source address and wildcard mask
Answer: D
Question 5
Refer to the exhibit.
Statements A, B, C, and D of ACL 10 have been entered in the shown order and applied to interface E0 inbound, to prevent all hosts (except those whose addresses are the first and last IP of subnet 172.21.1.128/28) from accessing the network. But as is, the ACL does not restrict anyone from the network. How can the ACL statements be re-arranged so that the system works as intended?
A. ACDB
B. BADC
C. DBAC
D. CDBA
Answer: D
Question 6
Which statement about access lists that are applied to an interface is true?
A. you can apply only one access list on any interface
B. you can configure one access list, per direction, per layer 3 protocol
C. you can place as many access lists as you want on any interface
D. you can configure one access list, per direction, per layer 2 protocol
Answer: B
Explanation
We can have only 1 access list per protocol, per direction and per interface. It means:
+ We can not have 2 inbound access lists on an interface
+ We can have 1 inbound and 1 outbound access list on an interface
Question 7
A network engineer wants to allow a temporary entry for a remote user with a specific username and password so that the user can access the entire network over the internet. Which ACL can be used?
A. reflexive
B. extended
C. standard
D. dynamic
Answer: D
Explanation
We can use a dynamic access list to authenticate a remote user with a specific username and password. The authentication process is done by the router or a central access server such as a TACACS+ or RADIUS server. The configuration of dynamic ACL can be read here: http://www.cisco.com/en/US/tech/tk58...80094524.shtml
Question 8
Which two statements about static NAT translations are true? (choose two)
A. They are always present in the NAT table.
B. They allow connection to be initiated from the outside.
C. They can be configured with access lists, to allow two or more connections to be initiated from the outside.
D. They require no inside or outside interface markings because addresses are statically defined.
Answer: A B
Explanation
With static NAT, translations exist in the NAT translation table as soon as you configure static NAT command(s), and they remain in the translation table until you delete the static NAT command(s).
With dynamic NAT, translations do not exist in the NAT table until the router receives traffic that requires translation. Dynamic translations have a timeout period after which they are purged from the translation table.
-> A is correct.
Because static NAT translations are always present in the NAT table so outside hosts can initiate the connection without being dropped -> B is correct.
Static translations can not be configured with access lists. To configure static NAT, we only need to specify source IP, NAT IP, inside interface & outside interface.
-> C is not correct.
We have to specify which is the inside and outside interface -> D is not correct.
For your information, below is an example of configuring static NAT:
R0(config)#int f0/0
R0(config-if)#ip nat inside
R0(config-if)#int f0/1
R0(config-if)#ip nat outside
R0(config)#ip nat inside source static 10.0.0.1 200.0.0.2
(Reference: http://www.cisco.com/en/US/tech/tk64...80093f31.shtml)
Question 9
What are two benefits of using NAT? (choose two)
A. NAT protects network security because private networks are not advertised.
B. NAT accelerates the routing process because no modifications are made on the packets.
C. Dynamic NAT facilitates connections from the outside of the network.
D. NAT facilitates end-to-end communication when IPsec is enable.
E. NAT eliminates the need to re-address all host that require external access.
F. NAT conserves addresses through host MAC-level multiplexing.
Answer: A E
Explanation
By not reveal the internal IP addresses, NAT adds some security to the inside network -> A is correct.
NAT has to modify the source IP addresses in the packets -> B is not correct.
Connection from the outside to a network through “NAT” is more difficult than a normal network because IP addresses of inside hosts are hidden -> C is not correct.
In order for IPsec to work with NAT we need to allow additional protocols, including Internet Key Exchange (IKE), Encapsulating Security Payload (ESP) and Authentication Header (AH) -> more complex -> D is not correct.
By allocating specific public IP addresses to inside hosts, NAT eliminates the need to re-address the inside hosts -> E is correct.
NAT does conserve addresses but not through host MAC-level multiplexing. It conserves addresses by allowing many private IP addresses to use the same public IP address to go to the Internet -> F is not correct.
Question 10
Refer to the exhibit. What statement is true of the configuration for this network?
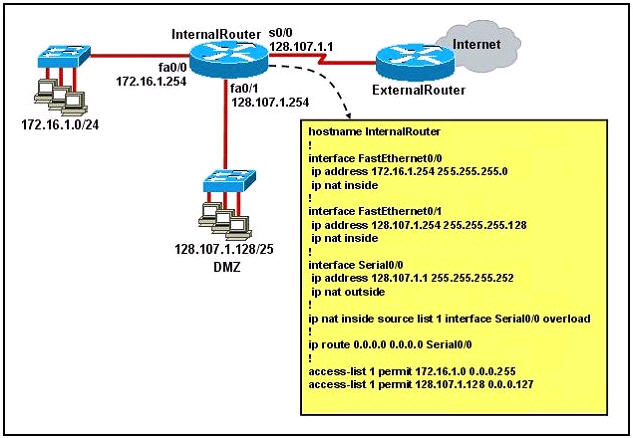
A. The configuration that is shown provides inadequate outside address space for translation of the number of inside addresses that are supported.
B. Because of the addressing on interface FastEthernet0/1, the Serial0/0 interface address will not support the NAT configuration as shown.
C. The number 1 referred to in the ip nat inside source command references access-list number 1.
D. ExternalRouter must be configured with static routers to network 172.16.2.0/24
Answer: C
Explanation
The “list 1″ refers to the access-list number 1.
Which item represents the standard IP ACL?
A. access-list 50 deny 192.168.1.1 0.0.0.255
B. access-list 110 permit ip any any
C. access-list 2500 deny tcp any host 192.168.1.1 eq 22
D. access-list 101 deny tcp any host 192.168.1.1
Answer: A
Explanation
The standard access lists are ranged from 1 to 99 and from 1300 to 1999 so only access list 50 is a standard access list.
Question 2
A network administrator is configuring ACLs on a Cisco router, to allow traffic from hosts on networks 192.168.146.0, 192.168.147.0, 192.168.148.0, and 192.168.149.0 only. Which two ACL statements, when combined, would you use to accomplish this task? (Choose two)
A. access-list 10 permit ip 192.168.146.0 0.0.1.255
B. access-list 10 permit ip 192.168.147.0 0.0.255.255
C. access-list 10 permit ip 192.168.148.0 0.0.1.255
D. access-list 10 permit ip 192.168.149.0 0.0.255.255
E. access-list 10 permit ip 192.168.146.0 0.0.0.255
F. access-list 10 permit ip 192.168.146.0 255.255.255.0
Answer: A C
Question 3
Refer to the exhibit.
| ACL 102 access-list 102 deny tcp 172.21.1.1 0.0.0.255 any eq 80 access-list 102 deny ip any any RouterA#show ip int FastEthernet0/0 is up, line protocol is up Internet address is 192.168.1.144/20 Broadcast address is 255.255.255.255 Address determined by DHCP MTU is 1500 bytes Helper address is not set Directed broadcast forwarding is enabled Outgoing access list is 102 Inbound access list is not set Proxy ARP is enabled |
A. no ip access-class 102 in
B. no ip access-class 102 out
C. no ip access-group 102 in
D. no ip access-group 102 out
E. no ip access-list 102 in
Answer: D
Question 4
On which options are standard access lists based?
A. destination address and wildcard mask
B. destination address and subnet mask
C. source address and subnet mask
D. source address and wildcard mask
Answer: D
Question 5
Refer to the exhibit.
| ACL 10 Statements are written in this order: A. permit any B. deny 172.21.1.128 0.0.0.15 C. permit 172.21.1.129 0.0.0.0 D. permit 172.21.1.142 0.0.0.0 |
A. ACDB
B. BADC
C. DBAC
D. CDBA
Answer: D
Question 6
Which statement about access lists that are applied to an interface is true?
A. you can apply only one access list on any interface
B. you can configure one access list, per direction, per layer 3 protocol
C. you can place as many access lists as you want on any interface
D. you can configure one access list, per direction, per layer 2 protocol
Answer: B
Explanation
We can have only 1 access list per protocol, per direction and per interface. It means:
+ We can not have 2 inbound access lists on an interface
+ We can have 1 inbound and 1 outbound access list on an interface
Question 7
A network engineer wants to allow a temporary entry for a remote user with a specific username and password so that the user can access the entire network over the internet. Which ACL can be used?
A. reflexive
B. extended
C. standard
D. dynamic
Answer: D
Explanation
We can use a dynamic access list to authenticate a remote user with a specific username and password. The authentication process is done by the router or a central access server such as a TACACS+ or RADIUS server. The configuration of dynamic ACL can be read here: http://www.cisco.com/en/US/tech/tk58...80094524.shtml
Question 8
Which two statements about static NAT translations are true? (choose two)
A. They are always present in the NAT table.
B. They allow connection to be initiated from the outside.
C. They can be configured with access lists, to allow two or more connections to be initiated from the outside.
D. They require no inside or outside interface markings because addresses are statically defined.
Answer: A B
Explanation
With static NAT, translations exist in the NAT translation table as soon as you configure static NAT command(s), and they remain in the translation table until you delete the static NAT command(s).
With dynamic NAT, translations do not exist in the NAT table until the router receives traffic that requires translation. Dynamic translations have a timeout period after which they are purged from the translation table.
-> A is correct.
Because static NAT translations are always present in the NAT table so outside hosts can initiate the connection without being dropped -> B is correct.
Static translations can not be configured with access lists. To configure static NAT, we only need to specify source IP, NAT IP, inside interface & outside interface.
-> C is not correct.
We have to specify which is the inside and outside interface -> D is not correct.
For your information, below is an example of configuring static NAT:
R0(config)#int f0/0
R0(config-if)#ip nat inside
R0(config-if)#int f0/1
R0(config-if)#ip nat outside
R0(config)#ip nat inside source static 10.0.0.1 200.0.0.2
(Reference: http://www.cisco.com/en/US/tech/tk64...80093f31.shtml)
Question 9
What are two benefits of using NAT? (choose two)
A. NAT protects network security because private networks are not advertised.
B. NAT accelerates the routing process because no modifications are made on the packets.
C. Dynamic NAT facilitates connections from the outside of the network.
D. NAT facilitates end-to-end communication when IPsec is enable.
E. NAT eliminates the need to re-address all host that require external access.
F. NAT conserves addresses through host MAC-level multiplexing.
Answer: A E
Explanation
By not reveal the internal IP addresses, NAT adds some security to the inside network -> A is correct.
NAT has to modify the source IP addresses in the packets -> B is not correct.
Connection from the outside to a network through “NAT” is more difficult than a normal network because IP addresses of inside hosts are hidden -> C is not correct.
In order for IPsec to work with NAT we need to allow additional protocols, including Internet Key Exchange (IKE), Encapsulating Security Payload (ESP) and Authentication Header (AH) -> more complex -> D is not correct.
By allocating specific public IP addresses to inside hosts, NAT eliminates the need to re-address the inside hosts -> E is correct.
NAT does conserve addresses but not through host MAC-level multiplexing. It conserves addresses by allowing many private IP addresses to use the same public IP address to go to the Internet -> F is not correct.
Question 10
Refer to the exhibit. What statement is true of the configuration for this network?

A. The configuration that is shown provides inadequate outside address space for translation of the number of inside addresses that are supported.
B. Because of the addressing on interface FastEthernet0/1, the Serial0/0 interface address will not support the NAT configuration as shown.
C. The number 1 referred to in the ip nat inside source command references access-list number 1.
D. ExternalRouter must be configured with static routers to network 172.16.2.0/24
Answer: C
Explanation
The “list 1″ refers to the access-list number 1.