Mục tiêu
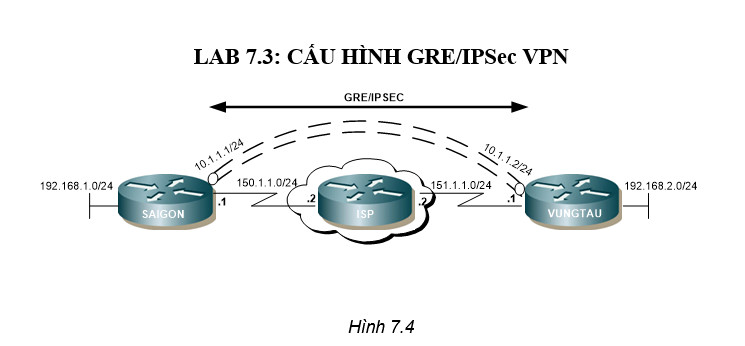
Cấu hình GRE cho phép giữa hai site có thể trao đổi thông tin định tuyến và đảm bảo việc giao giao tiếp giữa hai site được bảo vệ với IPSec. A) Cấu hình
Cấu hình chính sách ipsec:
SAIGON(config)#crypto ipsec transform-set MYSET esp-md5-hmac esp-des
SAIGON(cfg-crypto-trans)#mode transport
Xác định dữ liệu được bảo vệ. Vì quá trình đóng gói GRE xảy ra trước nên khi định nghĩa dữ liệu được mã hóa phải là GRE:
SAIGON(config)#access-list 100 permit gre host 150.1.1.1 host 151.1.1.1
Cấu hình giao thức định tuyến. Lưu ý không kích hoạt cổng bên ngoài (cổng nối với Internet) tham gia quá trình định tuyến:
SAIGON(config)#router ospf 1
SAIGON(config-router)#network 192.168.1.0 0.0.0.255 area 0
SAIGON(config-router)#network 10.1.1.0 0.0.0.255 area 0
Thực hiện cấu hình tương tự trên VUNGTAU
B) Cấu hình đầy đủ
SAIGON
Building configuration...
Current configuration : 1763 bytes
!
hostname SAIGON
!
crypto isakmp policy 10
hash md5
authentication pre-share
group 2
crypto isakmp key vnpro address 151.1.1.1
!
crypto ipsec transform-set MYSET esp-des esp-md5-hmac
mode transport
!
crypto map MYMAP 10 ipsec-isakmp
set peer 151.1.1.1
set transform-set MYSET
match address 100
!
interface Tunnel1
ip address 10.1.1.1 255.255.255.0
tunnel source Serial0/0
tunnel destination 151.1.1.1
!
interface Loopback0
ip address 192.168.1.1 255.255.255.0
!
interface FastEthernet0/0
no ip address
shutdown
duplex auto
speed auto
!
interface Serial0/0
ip address 150.1.1.1 255.255.255.0
clockrate 2000000
crypto map MYMAP
!
interface FastEthernet0/1
no ip address
shutdown
duplex auto
speed auto
!
!
router ospf 1
log-adjacency-changes
network 10.1.1.0 0.0.0.255 area 0
network 192.168.1.0 0.0.0.255 area 0
!
ip classless
ip route 0.0.0.0 0.0.0.0 150.1.1.2
!
!
access-list 100 permit gre host 150.1.1.1 host 151.1.1.1
!
!
end
VUNGTAU
Building configuration...
Current configuration : 1500 bytes
!
hostname VUNGTAU
!
!
crypto isakmp policy 10
hash md5
authentication pre-share
group 2
crypto isakmp key vnpro address 150.1.1.1
!
!
crypto ipsec transform-set MYSET esp-des esp-md5-hmac
mode transport
!
crypto map MYMAP 10 ipsec-isakmp
set peer 150.1.1.1
set transform-set MYSET
match address 100
!
!
interface Tunnel1
ip address 10.1.1.2 255.255.255.0
tunnel source Serial0/0
tunnel destination 150.1.1.1
!
interface Loopback0
ip address 192.168.2.1 255.255.255.0
!
interface FastEthernet0/0
no ip address
shutdown
duplex auto
speed auto
!
interface Serial0/0
ip address 151.1.1.1 255.255.255.0
clockrate 2000000
crypto map MYMAP
!
interface FastEthernet0/1
no ip address
shutdown
duplex auto
speed auto
!
interface Serial0/1
no ip address
shutdown
clockrate 2000000
!
router ospf 1
log-adjacency-changes
network 10.1.1.0 0.0.0.255 area 0
network 192.168.2.0 0.0.0.255 area 0
!
ip classless
ip route 0.0.0.0 0.0.0.0 151.1.1.2
!
access-list 100 permit gre host 151.1.1.1 host 150.1.1.1
!
!
end
ISP
Building configuration...
Current configuration : 980 bytes
!
hostname ISP
!
interface FastEthernet0/0
no ip address
shutdown
duplex auto
speed auto
!
interface Serial0/0
ip address 150.1.1.2 255.255.255.0
clockrate 2000000
!
interface FastEthernet0/1
no ip address
shutdown
duplex auto
speed auto
!
interface Serial0/1
ip address 151.1.1.2 255.255.255.0
clockrate 2000000
!
!
end
ISP#
ws D) Kiểm tra các thông số cấu hình
Kiểm tra thông tin sự hội tụ của OSPF
SAIGON#sh ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
192.168.2.1 0 FULL/ - 00:00:38 10.1.1.2 Tunnel1
SAIGON#sh ip ospf interface
Tunnel1 is up, line protocol is up
Internet Address 10.1.1.1/24, Area 0
Process ID 1, Router ID 192.168.1.1, Network Type POINT_TO_POINT, Cost: 11111
Transmit Delay is 1 sec, State POINT_TO_POINT,
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
oob-resync timeout 40
Hello due in 00:00:02
Index 2/2, flood queue length 0
Next 0x0(0)/0x0(0)
Last flood scan length is 1, maximum is 1
Last flood scan time is 4 msec, maximum is 4 msec
Neighbor Count is 1, Adjacent neighbor count is 1
Adjacent with neighbor 192.168.2.1
Suppress hello for 0 neighbor(s)
Loopback0 is up, line protocol is up
Internet Address 192.168.1.1/24, Area 0
Process ID 1, Router ID 192.168.1.1, Network Type LOOPBACK, Cost: 1
Loopback interface is treated as a stub Host
SAIGON#sh ip route
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is 150.1.1.2 to network 0.0.0.0
10.0.0.0/24 is subnetted, 1 subnets
C 10.1.1.0 is directly connected, Tunnel1
C 192.168.1.0/24 is directly connected, Loopback0
192.168.2.0/32 is subnetted, 1 subnets
O 192.168.2.1 [110/11112] via 10.1.1.2, 00:00:38, Tunnel1
150.1.0.0/24 is subnetted, 1 subnets
C 150.1.1.0 is directly connected, Serial0/0
S* 0.0.0.0/0 [1/0] via 150.1.1.2
Giao tiếp thành công giữa hai site
SAIGON#ping 192.168.2.1 source 192.168.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.2.1, timeout is 2 seconds:
Packet sent with a source address of 192.168.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 28/81/152 ms
Trạng thái ISAKMP SA và IPSec SA
SAIGON#sh crypto isakmp sa
dst src state conn-id slot
151.1.1.1 150.1.1.1 QM_IDLE 1 0
SAIGON#sh crypto ipsec sa
interface: Serial0/0
Crypto map tag: MYMAP, local addr. 150.1.1.1
protected vrf:
local ident (addr/mask/prot/port): (150.1.1.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (151.1.1.1/255.255.255.255/47/0)
current_peer: 151.1.1.1:500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 31, #pkts encrypt: 31, #pkts digest: 31
#pkts decaps: 23, #pkts decrypt: 23, #pkts verify: 23
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 3, #recv errors 0
local crypto endpt.: 150.1.1.1, remote crypto endpt.: 151.1.1.1
path mtu 1500, media mtu 1500
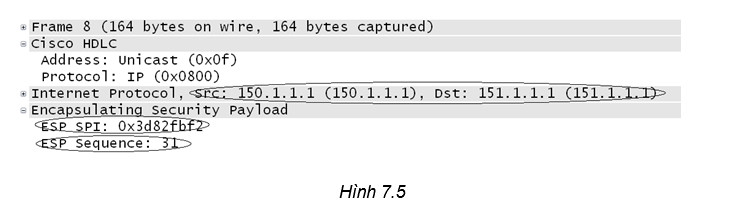
current outbound spi: 3D82FBF2
inbound esp sas:
spi: 0xE782E811(3884115985)
transform: esp-des esp-md5-hmac ,
in use settings ={Transport, }
slot: 0, conn id: 2000, flow_id: 1, crypto map: MYMAP
crypto engine type: Software, engine_id: 1
sa timing: remaining key lifetime (k/sec): (4452455/3561)
ike_cookies: 6346F52E 948175CB C36662EF 99F42E48
IV size: 8 bytes
replay detection support: Y
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x3D82FBF2(1031994354)
transform: esp-des esp-md5-hmac ,
in use settings ={Transport, }
slot: 0, conn id: 2001, flow_id: 2, crypto map: MYMAP
crypto engine type: Software, engine_id: 1
sa timing: remaining key lifetime (k/sec): (4452455/3561)
ike_cookies: 6346F52E 948175CB C36662EF 99F42E48
IV size: 8 bytes
replay detection support: Y
outbound ah sas:
outbound pcp sas:
Dữ liệu được bảo vệ với IPSec
- Giá trị ESP SPI của gói tin bằng với “outbound esp sas”
- Giá trị ESP Sequence tăng theo mỗi gói tin
SAIGON# sh crypto session
Crypto session current status
Interface: Serial0/0
Session status: UP-ACTIVE
Peer: 151.1.1.1/500
IKE SA: local 150.1.1.1/500 remote 151.1.1.1/500 Active
IPSEC FLOW: permit 47 host 150.1.1.1 host 151.1.1.1
Active SAs: 2, origin: crypto map