VPN REMOTE ACCESS
Mục tiêu
Tạo ra kênh secure VPN sử dụng IPSec giữa PC sử dụng phần mềm Cisco VPN Client và ASA5510
PC khi kết nối VPN tới ASA sẽ có IP nằm trong pool 20.0.2.20-20.0.2.50/24
Mô hình
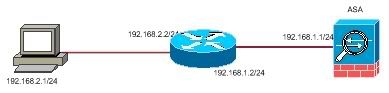
Cấu hình tham khảo
Router Cấu hình địa chỉ trên các interface
!
interface FastEthernet0/0
ip address 192.168.2.2 255.255.255.0
ip virtual-reassembly
speed auto
!
!
interface FastEthernet0/1
ip address 192.168.1.2 255.255.255.0
ip virtual-reassembly
speed auto
!
interface FastEthernet0/0
ip address 192.168.2.2 255.255.255.0
ip virtual-reassembly
speed auto
!
!
interface FastEthernet0/1
ip address 192.168.1.2 255.255.255.0
ip virtual-reassembly
speed auto
!
ASA
Bước 1 Cấu hình địa chỉ IP trên các interface, định tuyến
!
interface Ethernet0/0
nameif outside
security-level 0
ip address 192.168.1.1 255.255.255.0
!
interface Ethernet0/1
nameif inside
security-level 100
ip address 10.0.1.1 255.255.255.0
!
route outside 0.0.0.0 0.0.0.0 192.168.1.2 1
interface Ethernet0/0
nameif outside
security-level 0
ip address 192.168.1.1 255.255.255.0
!
interface Ethernet0/1
nameif inside
security-level 100
ip address 10.0.1.1 255.255.255.0
!
route outside 0.0.0.0 0.0.0.0 192.168.1.2 1
Bước 2: Tạo isakmp policy
ASA1(config)# isakmp policy 2
ASA1(config-isakmp-policy)# authentication pre-share
ASA1(config-isakmp-policy)# encryption des
ASA1(config-isakmp-policy)# hash md5
ASA1(config-isakmp-policy)# exit
ASA1(config-isakmp-policy)# authentication pre-share
ASA1(config-isakmp-policy)# encryption des
ASA1(config-isakmp-policy)# hash md5
ASA1(config-isakmp-policy)# exit
Bước 3: Enable isakmp trên interface outside
ASA1(config)#crypto isakmp identity address
ASA1(config)#crypto isakmp enable outside
ASA1(config)#crypto isakmp enable outside
Bước 4:
Tạo pool với tên là testpool có dãy địa chỉ trong khoảng 20.0.2.20-20.0.2.50/24 để cấp địa chỉ cho VPN client
ASA1(config)# ip local pool testpool 20.0.2.20-20.0.2.50
Tạo username/password cho VPN client được chứng thực trên local
ASA1(config)# username testuser password 123456789
Bước 5 Tạo transform-set với tên là myset
ASA1(config)# crypto ipsec transform-set myset esp-des esp-md5-hmac
Bước 6: Chọn tunnel-group type/attributes
ASA1(config)# tunnel-group testgroup type ipsec-ra
ASA1(config)# tunnel-group testgroup general-attributes
ASA1(config-tunnel-general)# address-pool testpool
ASA1(config-tunnel-general)# exit
ASA1(config)# tunnel-group testgroup general-attributes
ASA1(config-tunnel-general)# address-pool testpool
ASA1(config-tunnel-general)# exit
Bước 7: Tạo group cho user
ASA1(config)# tunnel-group testgroup ipsec-attributes
ASA1(config-tunnel-ipsec)# pre-shared-key cisco123
ASA1(config-tunnel-ipsec)# pre-shared-key cisco123
Bước 8: Tạo ACL cho interesting traffic
ASA1(config)# access-list vpnra permit ip 10.0.1.0 255.255.255.0 20.0.20.0 255.255.255.0
ASA1(config)# nat (inside) 0 access-list vpnra
ASA1(config)# nat (inside) 0 access-list vpnra
Bước 9: Tạo dynamic map
ASA1(config)# crypto dynamic-map dyn1 1 set transform-set myset
ASA1(config)# crypto dynamic-map dyn1 1 set reverse-route
ASA1(config)# crypto dynamic-map dyn1 1 set reverse-route
Bước 10: Tạo crypto map
ASA1(config)# crypto map mymap 10 ipsec-isakmp dynamic dyn1
Áp crypto map vào interface outside
ASA1(config)# crypto map mymap interface outside
VPN client
Bước 1:
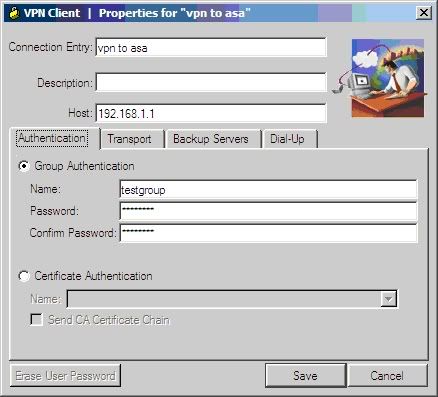
Bước 2: nhập username/password
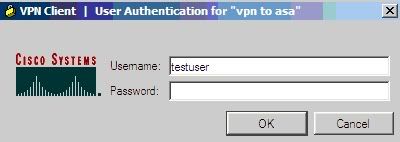
Username: testuser
Password: 123456789
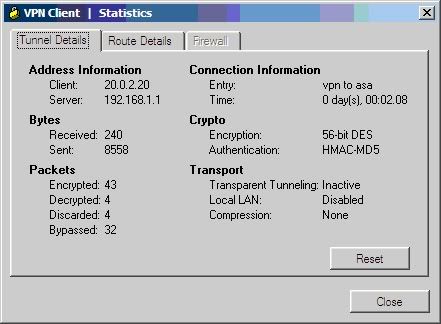
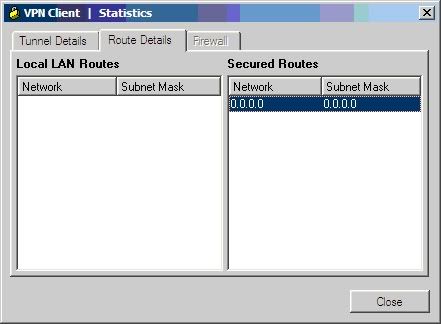
Sau khi chứng thực thành công sẽ tạo kết nối VPN
Kiểm tra
ASA1(config)# show ip local pool testpool
Begin End Mask Free In use
20.0.2.20 20.0.2.52 0.0.0.0 32 1
Available Addresses:
20.0.2.21
20.0.2.22
20.0.2.23
20.0.2.24
…
20.0.2.47
20.0.2.48
20.0.2.49
20.0.2.50
In Use Addresses:
20.0.2.20
ASA1(config)# show run isakmp
crypto isakmp identity address
crypto isakmp enable outside
crypto isakmp policy 2
authentication pre-share
encryption des
hash md5
group 2
lifetime 86400
ASA1(config)# show run crypto ipsec
crypto ipsec transform-set myset esp-des esp-md5-hmac
ASA1(config)# show run tunnel-group
tunnel-group testgroup type ipsec-ra
tunnel-group testgroup general-attributes
address-pool testpool
tunnel-group testgroup ipsec-attributes
pre-shared-key *
ASA1(config)# show run crypto map
crypto map mymap 10 ipsec-isakmp dynamic dyn1
crypto map mymap interface outside
Begin End Mask Free In use
20.0.2.20 20.0.2.52 0.0.0.0 32 1
Available Addresses:
20.0.2.21
20.0.2.22
20.0.2.23
20.0.2.24
…
20.0.2.47
20.0.2.48
20.0.2.49
20.0.2.50
In Use Addresses:
20.0.2.20
ASA1(config)# show run isakmp
crypto isakmp identity address
crypto isakmp enable outside
crypto isakmp policy 2
authentication pre-share
encryption des
hash md5
group 2
lifetime 86400
ASA1(config)# show run crypto ipsec
crypto ipsec transform-set myset esp-des esp-md5-hmac
ASA1(config)# show run tunnel-group
tunnel-group testgroup type ipsec-ra
tunnel-group testgroup general-attributes
address-pool testpool
tunnel-group testgroup ipsec-attributes
pre-shared-key *
ASA1(config)# show run crypto map
crypto map mymap 10 ipsec-isakmp dynamic dyn1
crypto map mymap interface outside
VPN client
Comment